Office Building Security Systems: Layered Protection Strategies for 2026

Office Building Security Systems: Layered Protection Strategies for 2026
A single point of failure in office security can cost businesses an average of $200,000 per incident, according to recent commercial security data. Yet many South Florida office buildings still rely on outdated single-layer protection that leaves critical vulnerabilities exposed. The evolving threat landscape of 2026 demands a fundamentally different approach: layered security systems that create multiple defensive barriers between potential threats and your most valuable assets.
Modern office building security systems have evolved far beyond basic locks and cameras. Today’s professional-grade solutions integrate multiple technologies into cohesive networks that detect, deter, and document security events while providing seamless access for authorized personnel. This comprehensive approach to security systems for businesses transforms your office building from a vulnerable target into a hardened facility that actively protects people, property, and proprietary information.
Understanding the Layered Security Philosophy
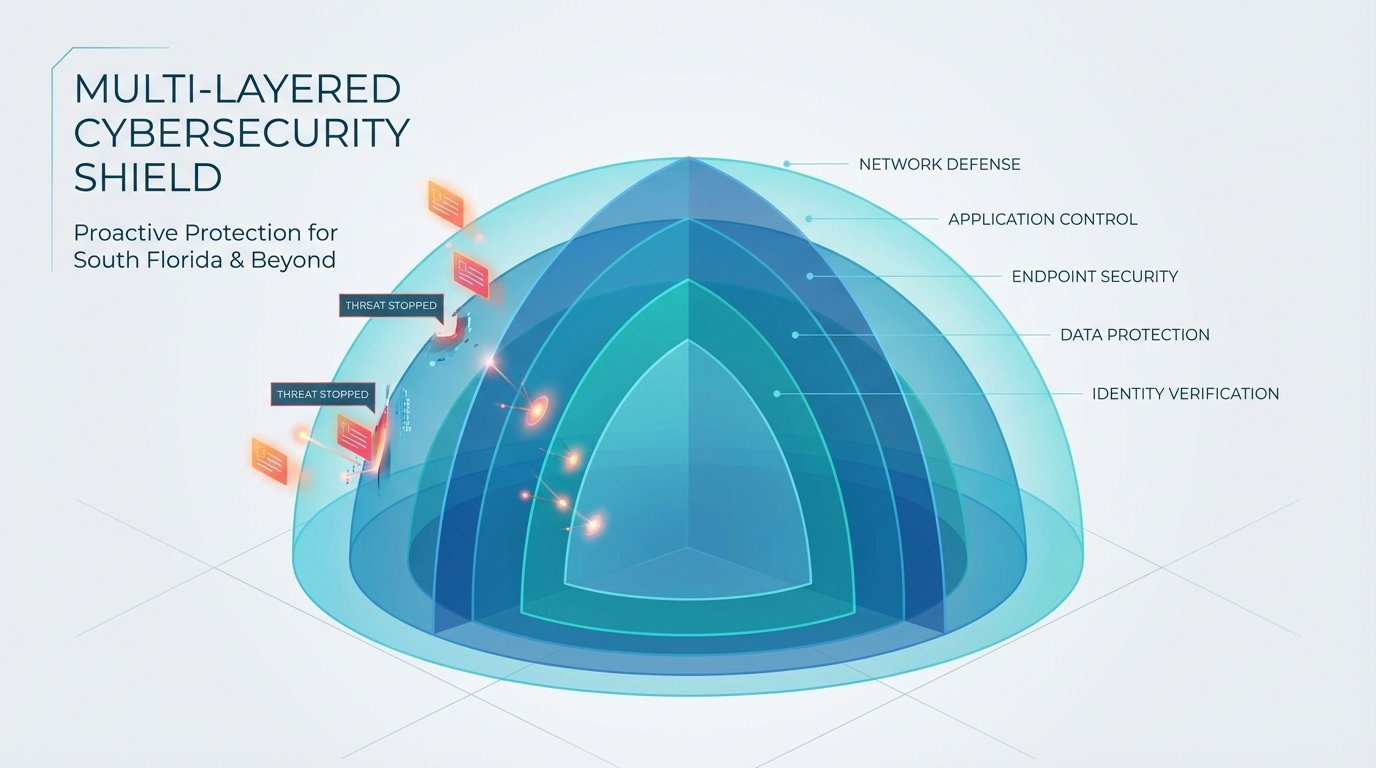
Layered security, also known as defense in depth, operates on a simple principle: if one security measure fails, additional layers provide backup protection. This redundancy creates a security posture exponentially stronger than any single system could achieve alone.
The concept originates from military and critical infrastructure protection strategies but has become essential for commercial office buildings in 2026. Each layer addresses different threat vectors and failure modes, ensuring that no single vulnerability compromises your entire security infrastructure.
The Three Core Perimeters
Effective office building security systems establish three distinct security perimeters:
- Exterior Perimeter: Property boundaries, parking areas, and building approaches where initial threat detection occurs
- Building Envelope: Entry points including doors, windows, loading docks, and roof access where physical access control prevents unauthorized entry
- Interior Zones: Critical areas within the building such as server rooms, executive offices, and storage facilities requiring additional protection
Each perimeter employs different technologies working in concert to create a comprehensive security posture that adapts to your building’s unique risk profile and operational requirements.
Layer One: Intelligent Video Surveillance Systems
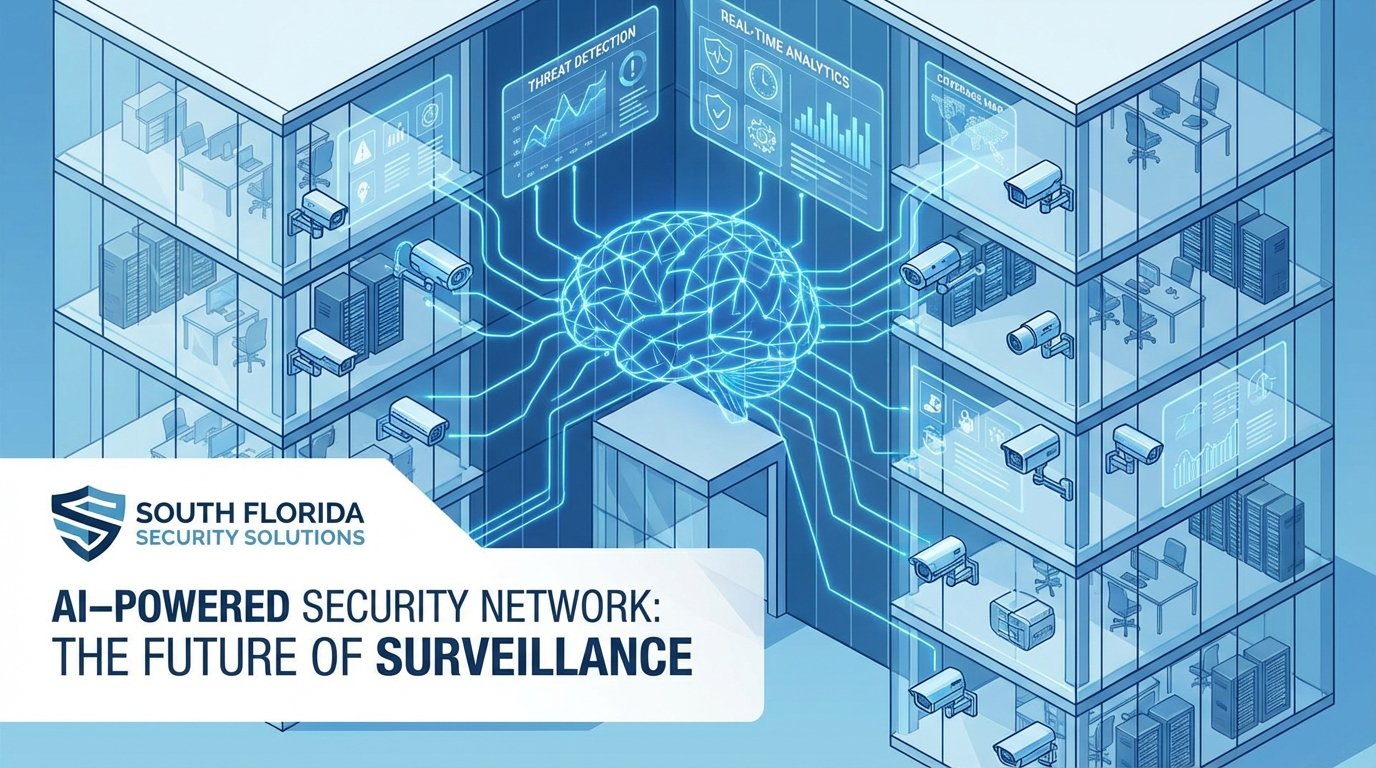
Professional security camera installation forms the foundation of modern office building security by providing continuous monitoring, forensic documentation, and increasingly sophisticated threat detection capabilities.
The video surveillance landscape has transformed dramatically in recent years. Today’s enterprise-grade systems leverage artificial intelligence and advanced analytics to actively identify security concerns rather than simply recording footage for later review.
Strategic Camera Placement
Effective professional security camera installation requires careful analysis of your building’s specific vulnerabilities. Critical coverage areas include:
- All building entry and exit points with facial recognition capabilities
- Parking areas and vehicle approaches with license plate recognition
- Loading docks and service entrances where theft incidents frequently occur
- Common areas including lobbies, elevators, and stairwells
- Perimeter fencing and property boundaries
- Critical interior zones containing sensitive assets or information
Modern 4K and higher-resolution cameras capture details that were impossible to discern with older analog systems. License plate numbers, facial features, and small objects are clearly visible even when digitally zooming into recorded footage, providing law enforcement with actionable evidence when incidents occur.
AI-Powered Analytics
The most significant advancement in business security system installation south florida has been the integration of artificial intelligence into video surveillance. Contemporary systems can identify unusual patterns, detect unauthorized access attempts, recognize known individuals, and alert security personnel to potential threats in real-time.
These capabilities include loitering detection, crowd formation analysis, abandoned object identification, and perimeter breach alerts. The systems learn normal patterns for your facility and flag deviations that may indicate security concerns, dramatically reducing the burden on security personnel while improving response times.
Layer Two: Access Control Service Integration
While cameras observe and record, access control service systems actively prevent unauthorized entry by managing who can enter specific areas and when those permissions are valid. This physical barrier represents perhaps the most critical layer in your security infrastructure.
Modern access control has evolved from simple card readers to sophisticated biometric systems that verify identity with near-perfect accuracy while maintaining detailed audit trails of all access events.
Credential Technologies
Today’s access control service options include multiple credential technologies, each offering different security levels and user convenience:
- Mobile Credentials: Smartphone-based access using encrypted Bluetooth or NFC technology eliminates physical cards while providing enhanced security
- Biometric Verification: Fingerprint, facial recognition, and iris scanning systems confirm identity without relying on cards or devices that can be lost or stolen
- Multi-Factor Authentication: Combining credentials (something you have) with biometrics (something you are) or PIN codes (something you know) creates virtually impenetrable access control
- Smart Cards: RFID and NFC-enabled cards remain popular for their balance of security, cost, and ease of use
The ideal solution often combines multiple technologies, using higher-security biometric verification for sensitive areas while employing convenient mobile credentials for general building access.
Zone-Based Security Architecture
Sophisticated office building security systems implement zone-based access control that grants different permissions based on roles, departments, and clearance levels. Your accounting staff might access the finance department but not engineering labs, while maintenance personnel receive time-limited access to all areas during their shifts.
This granular control extends to temporal restrictions as well. Access permissions can automatically adjust based on time of day, day of week, or special schedules. After-hours access triggers additional verification requirements or notifies security personnel, creating dynamic security that adapts to your building’s operational patterns.
Layer Three: Intrusion Detection Systems
Intrusion detection provides the critical third layer by monitoring the building envelope for forced entry attempts, detecting breaches that bypass access control systems, and alerting security personnel to unauthorized access through windows, doors, or other entry points.
Modern intrusion systems integrate seamlessly with access control and video surveillance, creating an interconnected security ecosystem where each component enhances the others’ effectiveness.
Detection Technologies
Contemporary intrusion detection employs multiple sensor technologies:
- Door and Window Contacts: Magnetic sensors detect when protected openings are breached
- Glass Break Detectors: Acoustic sensors identify the specific sound frequency of breaking glass
- Motion Sensors: Advanced PIR and microwave detectors identify movement in protected spaces while filtering false alarms from HVAC systems and environmental factors
- Vibration Sensors: Detect forced entry attempts on walls, ceilings, and floors
- Environmental Monitoring: Water detection, temperature extremes, and smoke detection protect against non-security threats that can damage property and disrupt operations
These sensors connect to a central monitoring system that processes alerts, verifies threats through video surveillance, and initiates appropriate responses including notifying security personnel, locking down specific zones, or contacting law enforcement.
Layer Four: Visitor Management Systems
Visitors represent a unique security challenge for office buildings. They require temporary access but shouldn’t receive the same privileges as employees. Professional visitor management systems address this challenge while creating positive first impressions for clients, vendors, and guests.
Modern systems capture visitor information, photograph guests, print temporary badges, notify hosts of visitor arrivals, and maintain comprehensive logs of all visitor activity. Integration with access control systems allows temporary credentials to be instantly deactivated when visits conclude.
Advanced implementations include pre-registration capabilities where expected visitors receive QR codes for expedited check-in, watchlist screening that flags individuals of concern, and health screening features that have become increasingly important in recent years.
Layer Five: Cybersecurity for Physical Security Systems
As office building security systems become increasingly networked and intelligent, they also become potential targets for cyber attacks. A compromised security system is worse than no system at all, providing false confidence while attackers exploit vulnerabilities.
Professional business security system installation south florida must include robust cybersecurity measures protecting the security infrastructure itself:
- Network segmentation isolating security systems from general IT networks
- Encrypted communications between all system components
- Strong authentication requirements for system administration
- Regular firmware updates and security patches
- Intrusion detection monitoring the security network itself
- Redundant backup systems ensuring continued operation during cyber incidents
The convergence of physical and cybersecurity represents one of the most significant developments in commercial security. Your security integrator should demonstrate expertise in both domains, ensuring that sophisticated physical security measures aren’t undermined by inadequate network protection.
Integration: Making Layers Work Together
Individual security layers provide value, but true protection emerges when these systems integrate into a unified security ecosystem. Integration enables automated responses, reduces false alarms, and provides security personnel with comprehensive situational awareness.
Automated Response Protocols
When an intrusion sensor triggers, integrated systems automatically direct nearby cameras to the alert location, lock adjacent doors to contain the threat, notify security personnel with real-time video feeds, and create detailed incident reports. These automated responses occur in seconds, far faster than any human operator could manually coordinate multiple systems.
Similarly, when an employee uses their access credential at an unusual time, the system can require additional verification, alert security staff, and begin recording their movements through the building. These conditional responses adapt security levels to match threat indicators.
Centralized Management Platforms
Modern office building security systems consolidate all security functions into unified management platforms that provide single-pane-of-glass visibility across your entire security infrastructure. Security personnel monitor access control events, review camera feeds, respond to intrusion alerts, and manage visitor registration from a single interface.
These platforms leverage cloud connectivity for remote monitoring and management, allowing security teams to respond to incidents regardless of their physical location. Mobile applications provide incident notifications and emergency response capabilities directly to smartphones and tablets.
Compliance and Regulatory Considerations
Many South Florida businesses must comply with industry-specific security regulations. Healthcare facilities face HIPAA requirements, financial institutions must meet GLBA standards, and government contractors navigate NIST guidelines. Professional security systems for businesses should be designed with compliance requirements as core considerations rather than afterthoughts.
Comprehensive audit trails documenting all access events, visitor activities, and security incidents provide the documentation required for compliance verification and incident investigation. Data retention policies ensure footage and access logs are maintained for required periods while protecting privacy through appropriate access controls.
Scalability and Future-Proofing
Office buildings evolve. Tenant requirements change, organizations grow, and security threats develop. Security systems installed today must accommodate tomorrow’s needs without requiring complete replacement.
Professional security integrators design systems with expansion in mind, specifying infrastructure that supports additional cameras, readers, and sensors as needs grow. Open-protocol systems avoid vendor lock-in, ensuring you can upgrade components without replacing entire systems.
Cloud-based architectures provide particularly strong future-proofing benefits. New features and capabilities deploy through software updates rather than hardware replacement. Artificial intelligence algorithms improve continuously, enhancing threat detection without touching existing cameras or sensors.
Selecting Professional Security Integration Partners
The sophistication of modern security systems for businesses demands professional expertise. DIY approaches and consumer-grade equipment simply cannot deliver the reliability, integration, and support that office building security requires.
When evaluating security integration companies, consider these factors:
- Licensing and certifications demonstrating technical competence and legal compliance
- Experience with commercial installations of similar scale and complexity
- Manufacturer certifications from leading security technology vendors
- References from existing clients with comparable facilities
- Service and support capabilities including 24/7 emergency response
- Cybersecurity expertise protecting both physical and network security
- Long-term viability ensuring your integrator will support systems for years to come
The relationship with your security integrator extends far beyond initial installation. Ongoing maintenance, system updates, user training, and emergency support make this partnership critical to long-term security effectiveness.
Investment Considerations and ROI
Comprehensive office building security systems represent significant investments, but the costs of inadequate security far exceed properly designed protection. Beyond direct losses from theft and vandalism, security incidents create liability exposure, operational disruption, reputational damage, and potential regulatory penalties.
Professional systems also deliver operational benefits that offset security costs. Access control eliminates expensive lock rekeying when employees leave or keys are lost. Automated visitor management reduces reception staff workload. Video surveillance resolves workplace disputes and fraudulent injury claims. Energy management integration reduces utility costs by coordinating lighting and HVAC with occupancy patterns detected by security sensors.
Many businesses find that comprehensive security systems deliver positive ROI through operational benefits alone, making the security value essentially free.
Taking Action: Implementing Layered Security
Transforming your office building security from vulnerable single-layer protection to comprehensive defense in depth begins with professional security assessment. Qualified integrators evaluate your facility’s unique risks, identify vulnerabilities in existing systems, and design layered solutions addressing your specific security requirements and operational constraints.
This assessment considers numerous factors including building architecture, occupancy patterns, asset values, regulatory requirements, and threat profiles specific to your location and industry. The resulting security design balances protection effectiveness with operational convenience and budget realities.
Implementation typically proceeds in phases, allowing you to prioritize critical vulnerabilities while spreading investment over time. Core infrastructure including network cabling and control systems deploys first, followed by cameras, access control, and intrusion detection according to risk-based priorities.
Protecting Your South Florida Office Building
The security challenges facing South Florida office buildings in 2026 demand sophisticated, multi-layered protection that adapts to evolving threats while supporting daily operations. Single-purpose systems and outdated technology no longer provide adequate protection for valuable assets, sensitive information, and most importantly, the people working in your facility.
Professional business security system installation south florida creates integrated security ecosystems where intelligent cameras, robust access control service, comprehensive intrusion detection, visitor management, and cybersecurity protections work together as force multipliers. Each layer compensates for potential weaknesses in others while contributing unique capabilities that enhance overall security effectiveness.
TechPro Security Products specializes in designing and implementing layered security solutions for South Florida office buildings. Our licensed security integration professionals bring decades of experience protecting commercial facilities with sophisticated, professionally installed systems that deliver reliable protection and operational value. We provide comprehensive access control service, professional security camera installation, intrusion detection, and integrated security solutions tailored to your facility’s unique requirements.
Contact TechPro Security Products today for a professional security assessment of your office building. We’ll evaluate your current security posture, identify vulnerabilities, and design a layered protection strategy that safeguards your people, property, and business operations with the most advanced security systems for businesses available in 2026.