6 Security Vulnerabilities in Wireless Camera Systems
A property management company in Miami Beach discovered unauthorized users accessing their wireless camera feeds after noticing unfamiliar IP addresses in their system logs. Their parking garage cameras, meant to protect tenant vehicles, had become a security liability instead of an asset. This scenario plays out more often than security professionals would like to admit, as wireless camera systems introduce unique cybersecurity challenges that many organizations fail to address.
Wireless surveillance technology offers undeniable convenience and installation flexibility, but these benefits come with inherent security risks that demand professional attention. Understanding wireless camera security risks helps organizations make informed decisions about protecting their infrastructure and data.
Understanding Wireless Camera System Architecture
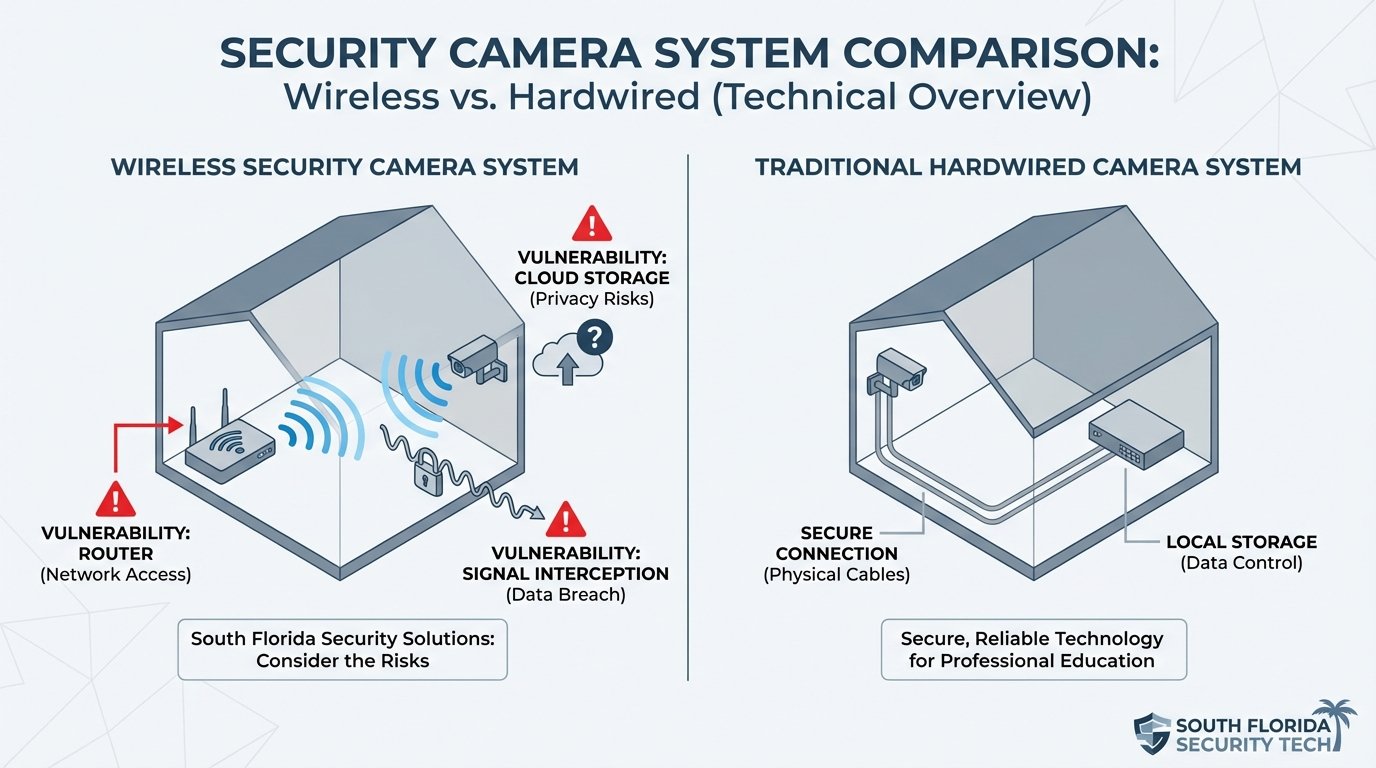
Wireless security cameras transmit video data over WiFi networks rather than through physical cables. This fundamental difference creates multiple points where security breaches can occur. Unlike traditional hardwired systems where an intruder would need physical access to cables, wireless systems broadcast signals that can potentially be intercepted from a distance.
Modern wireless cameras typically connect to local networks, cloud storage platforms, or both. Each connection point represents a potential vulnerability that requires proper security protocols. Professional-grade systems employ multiple layers of protection, while consumer devices often leave critical security gaps that sophisticated attackers can exploit.
Vulnerability #1: Weak or Default Authentication Credentials

The most common and easily exploitable weakness in wireless surveillance systems involves inadequate password protection. Manufacturers often ship cameras with default usernames like “admin” and passwords like “12345” or “password.” Security researchers have documented thousands of compromised cameras whose owners never changed these factory settings.
Attackers use automated tools that scan internet-connected devices, attempting known default credentials across thousands of IP addresses simultaneously. Once they gain access, they can view live feeds, access recorded footage, disable cameras during criminal activity, or use compromised devices as entry points to broader network attacks.
Professional Authentication Standards
Enterprise-grade wireless camera systems require complex password policies enforced at the system level. These standards include minimum character lengths, combination requirements for uppercase, lowercase, numbers, and special characters, and mandatory password rotation schedules. Multi-factor authentication adds another critical security layer, requiring physical tokens or mobile device verification beyond traditional passwords.
Commercial installations should implement role-based access control, ensuring employees only access camera feeds relevant to their responsibilities. A front desk attendant might need access to lobby cameras but not executive floor surveillance, for example.
Vulnerability #2: Unencrypted Video Transmission
WiFi camera vulnerabilities become particularly serious when video streams travel across networks without encryption. Unencrypted transmission means anyone intercepting the signal can view the footage in real-time. This risk extends beyond privacy concerns to include competitive intelligence theft, reconnaissance for criminal activity, and exposure of sensitive business operations.
Many budget wireless cameras transmit data “in the clear” without any encryption protocol. Even when cameras support encryption, improper configuration often leaves these features disabled. Attackers positioned within WiFi range can use readily available packet-sniffing software to capture and reconstruct video streams.
Encryption Protocols That Matter
Professional wireless surveillance systems employ end-to-end encryption using industry-standard protocols. WPA3 encryption for WiFi connections provides the strongest currently available wireless security, significantly improving upon older WPA2 standards. Transport Layer Security (TLS) 1.3 or higher protects data traveling between cameras and recording devices or cloud platforms.
Properly configured systems encrypt video both during transmission and while stored on local drives or cloud servers. This comprehensive approach ensures footage remains protected throughout its entire lifecycle, from capture through long-term archival.
Vulnerability #3: Outdated Firmware and Software
Security camera hacking frequently exploits known vulnerabilities that manufacturers have already patched. When organizations fail to update camera firmware regularly, they leave documented security holes open for attackers to exploit. Research shows that 60-70% of IoT devices, including security cameras, run outdated firmware with known security flaws.
Firmware updates address newly discovered vulnerabilities, improve encryption methods, and patch security holes that attackers have learned to exploit. Manufacturers release these updates reactively, often after security researchers or actual breaches expose weaknesses. The window between vulnerability discovery and patch implementation represents a critical risk period.
Enterprise Update Management
Professional security integrators implement centralized firmware management systems that monitor available updates and deploy them across entire camera networks simultaneously. These systems test updates in controlled environments before widespread deployment, ensuring new firmware doesn’t introduce operational issues.
Automated update scheduling performs installations during off-peak hours to minimize disruption. Documentation tracks which firmware versions run on each device, creating an audit trail for compliance requirements and troubleshooting purposes.
Vulnerability #4: Insecure Network Configuration
IP camera cybersecurity depends heavily on proper network architecture. Many organizations make the critical mistake of connecting wireless cameras directly to their primary business networks. This configuration allows compromised cameras to serve as launching points for attacks against other network resources, including file servers, workstations, and financial systems.
Wireless networks inherently broadcast signals beyond physical building boundaries. In dense commercial areas or multi-tenant buildings, multiple wireless networks overlap, creating opportunities for signal interception and man-in-the-middle attacks. Without proper network segmentation and access controls, a single compromised camera can expose an entire infrastructure.
Network Segmentation Best Practices
Professional installations place surveillance systems on isolated network segments, completely separated from business operations networks. Virtual Local Area Networks (VLANs) create logical separations even when devices share physical infrastructure. Firewalls between segments enforce strict communication rules, allowing camera traffic to reach recording systems while blocking unauthorized access attempts.
Network Access Control (NAC) systems authenticate devices before allowing network connections. These systems verify that connecting cameras match approved device profiles, preventing rogue devices from joining surveillance networks. MAC address filtering provides an additional authentication layer, though it shouldn’t serve as the sole security measure.
Vulnerability #5: Cloud Service Dependencies and Third-Party Risks
Modern wireless surveillance systems increasingly rely on cloud platforms for storage, remote access, and advanced analytics. These dependencies introduce wireless surveillance risks beyond an organization’s direct control. Cloud service vulnerabilities, data breaches at third-party providers, or service discontinuations can all compromise security and surveillance capabilities.
When cameras transmit footage to cloud platforms, that data travels across public internet infrastructure. Even with encryption, this transmission model increases exposure compared to closed, local systems. Cloud platforms also aggregate video from thousands of customers, making them attractive targets for large-scale attacks.
Vendor Security Assessment
Professional security implementations require thorough vendor vetting before adopting cloud-based surveillance platforms. Key evaluation criteria include SOC 2 Type II compliance certification, data encryption methods both in transit and at rest, geographic data storage locations and jurisdiction considerations, incident response plans and breach notification procedures, and data retention and deletion policies.
Service level agreements should explicitly define security responsibilities, uptime guarantees, and support response times. Understanding which security measures the vendor manages versus which remain the customer’s responsibility prevents dangerous security gaps.
Vulnerability #6: Physical Security of Wireless Infrastructure
Wireless cameras themselves require physical security protection. Unlike hardwired cameras where cutting cables immediately alerts monitoring systems, wireless cameras can be disabled through radio frequency jamming or simple power interruption without necessarily triggering alarms. Attackers with physical access can reset devices to factory defaults, install modified firmware, or simply redirect cameras away from areas they want to avoid.
Wireless access points and network equipment supporting camera systems also present physical vulnerability targets. An attacker gaining access to a network closet could compromise entire surveillance systems, intercept credentials, or install devices that capture all network traffic.
Tamper Detection and Physical Hardening
Enterprise wireless camera systems incorporate tamper-evident enclosures that trigger alerts when opened. Cameras installed in accessible locations require vandal-resistant housings that prevent easy disabling. Backup power supplies maintain camera operation during power disruptions, whether accidental or intentional.
Critical infrastructure equipment belongs in locked, access-controlled spaces with their own surveillance coverage. Environmental monitoring alerts administrators to unauthorized access attempts, temperature changes that might indicate equipment problems, or other anomalous conditions.
Regulatory Compliance and Legal Considerations
Organizations operating wireless surveillance systems must navigate increasingly complex regulatory requirements. Data privacy laws like GDPR, CCPA, and industry-specific regulations impose strict requirements on video data collection, storage, and access. Security vulnerabilities that lead to unauthorized footage access can trigger significant legal liability and regulatory penalties.
Florida state law requires businesses to implement reasonable security measures for personal information, which can include surveillance footage showing individuals. Healthcare facilities, financial institutions, and other regulated industries face additional compliance requirements that demand robust security controls.
Documentation and Audit Trails
Professional installations maintain comprehensive documentation showing security measures implementation, access control policies, employee training on proper system use, and incident response procedures. Automated logging systems track who accessed which camera feeds and when, creating audit trails for compliance verification and security investigations.
Professional Assessment and Risk Mitigation
Addressing wireless camera security risks requires specialized expertise that extends beyond basic IT knowledge. Professional security integrators conduct comprehensive vulnerability assessments that examine authentication mechanisms, encryption implementation, network architecture, physical security measures, vendor security practices, and compliance requirements.
These assessments identify specific vulnerabilities within existing systems and prioritize remediation efforts based on risk severity and potential business impact. Not all vulnerabilities carry equal weight—a weakness allowing unauthorized footage access poses different risks than one enabling broader network compromise.
Ongoing Security Management
Surveillance system security isn’t a one-time implementation but an ongoing process. Threat landscapes evolve constantly as attackers develop new exploitation techniques and researchers discover new vulnerabilities. Regular security audits, typically conducted annually or after significant system changes, ensure protection measures remain effective against current threats.
Penetration testing by qualified security professionals simulates real-world attack scenarios to identify weaknesses before malicious actors exploit them. These controlled tests reveal how quickly attackers could compromise systems and what damage they could inflict, informing security improvement priorities.
Balancing Security With Usability
Implementing comprehensive security measures requires careful balance with operational usability. Excessively restrictive security controls frustrate legitimate users and often lead to workarounds that undermine protection. Effective security architecture provides robust protection while maintaining reasonable access for authorized personnel.
Professional system design considers actual usage patterns and operational requirements. A retail business needs different access models than a corporate office or residential community. Security measures should align with genuine risk profiles rather than applying one-size-fits-all approaches.
The Case for Professional Installation and Management
While wireless camera technology appears straightforward, proper security implementation demands expertise across networking, cybersecurity, physical security, and regulatory compliance. DIY installations and consumer-grade equipment rarely incorporate the security layers necessary for protecting against determined attackers or meeting compliance requirements.
Licensed security integrators bring specialized knowledge of current threats, proven mitigation strategies, and experience designing systems that balance security with usability. Professional installation ensures proper configuration from initial deployment, avoiding the security holes that plague hastily implemented systems.
Ongoing professional management keeps systems updated against emerging threats, monitors for security incidents, and adjusts configurations as business needs evolve. This proactive approach prevents the security decay that occurs when systems operate without expert oversight.
Frequently Asked Questions
Can wireless security cameras be hacked?
Yes, wireless security cameras can be hacked through various methods including exploiting weak passwords, intercepting unencrypted transmissions, or leveraging known firmware vulnerabilities. Professional systems with proper security configurations significantly reduce these risks through multi-layered protection.
How can I tell if my wireless cameras have been compromised?
Signs of compromise include unusual network activity, unexpected camera movements or setting changes, unfamiliar users in access logs, and device performance degradation. Professional monitoring systems detect these anomalies automatically and trigger alerts for investigation.
Are wired cameras more secure than wireless cameras?
Wired cameras eliminate wireless interception risks but aren’t inherently immune to hacking. Both technologies require proper security measures. Professional-grade wireless systems with comprehensive security implementations can match or exceed the security of basic wired systems.
What encryption should wireless security cameras use?
Professional wireless cameras should use WPA3 for WiFi connections and TLS 1.3 for data transmission to recording or cloud platforms. End-to-end encryption ensures video remains protected throughout capture, transmission, and storage.
Protecting Your Investment and Your Security
Wireless surveillance systems offer valuable security capabilities when properly implemented and maintained. Understanding these six critical vulnerabilities provides the foundation for making informed decisions about system design, vendor selection, and security measures. The convenience of wireless technology doesn’t require accepting unnecessary risks—professional implementation delivers both flexibility and robust protection.
Organizations serious about security recognize that surveillance systems themselves must be secured against compromise. The cameras protecting your property shouldn’t simultaneously create new vulnerabilities that attackers can exploit.
TechPro Security Products specializes in designing and implementing secure wireless surveillance systems for South Florida businesses and organizations. Our licensed security professionals conduct comprehensive vulnerability assessments, implement enterprise-grade security measures, and provide ongoing system management that keeps your surveillance infrastructure protected against evolving threats. Contact us today to schedule a professional security evaluation and discover how properly configured wireless camera systems deliver both convenience and confidence.

